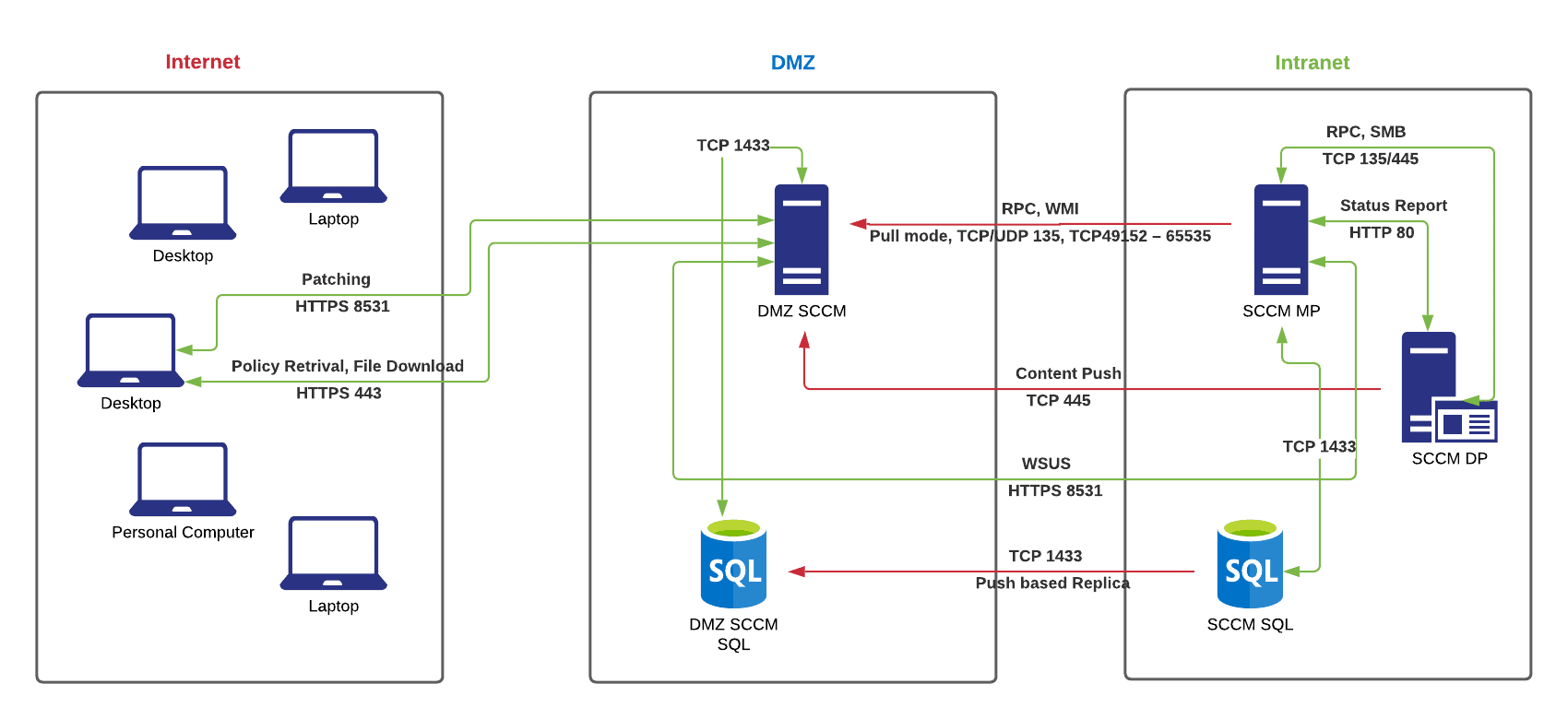
I tried to setup the SCCM as secure as possible for our internet facing clients, and here are two architect diagram by using IBCM(Internet Base Client Management) and Microsoft’s new Cloud Management Gateway.
For IBCM, we need to open a few ports:
SCCM MP -> DMZ SCCM ( TCP/UDP 135, TCP 49152-65535) ;
SCCM DP -> DMZ SCCM (TCP 445, SMB);
SCCM SQL -> DMZ SQL(TCP 1433);
and two way for:
SCCM WSUS < – > DMZ WSUS (HTTPS8531)
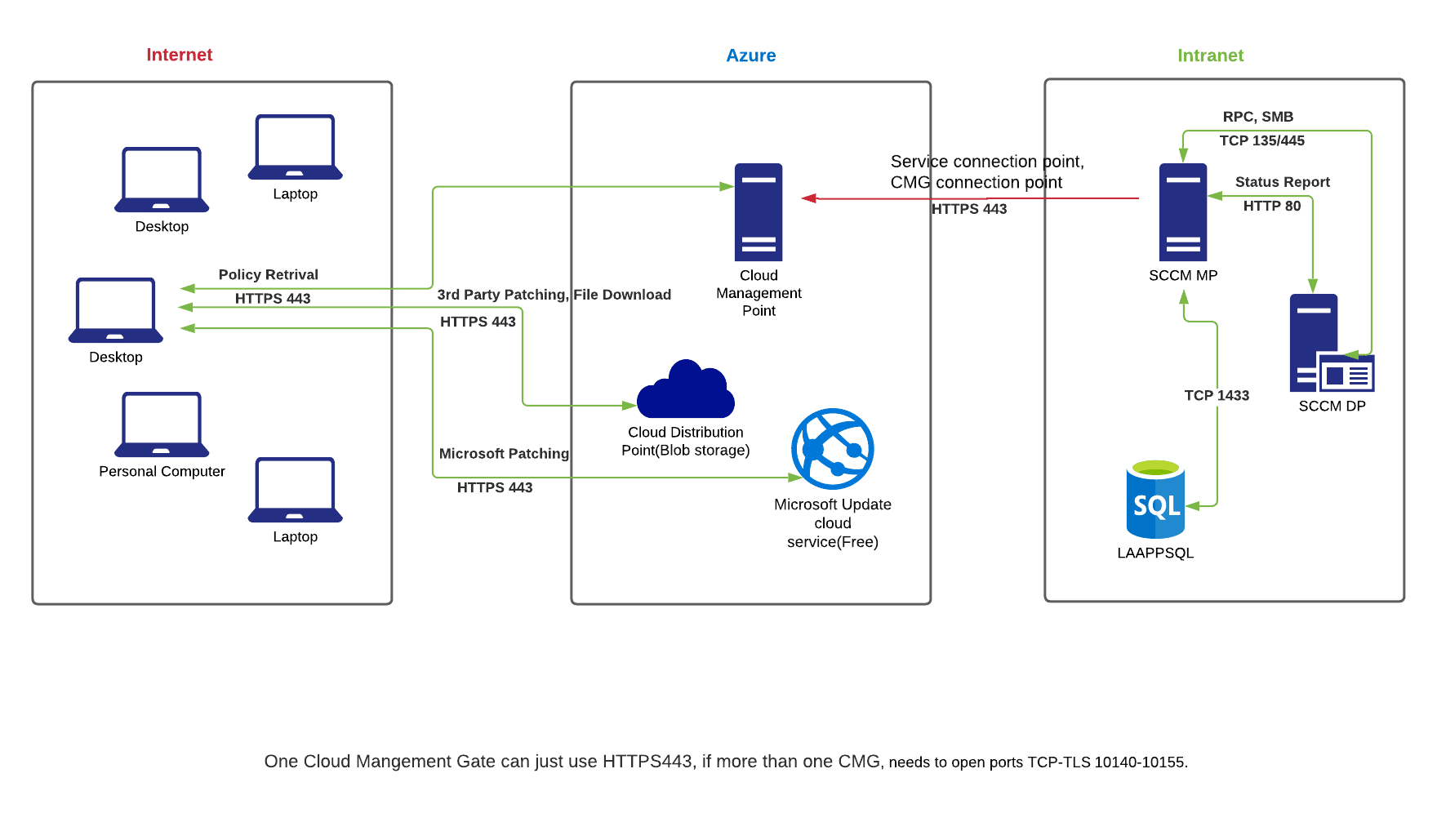
For Cloud Management Gate, it is a much nicer map:
SCCM MP -> Azure Cloud (HTTPS 443)
If you have more than one CMG, then have to open ports (10140-10155, one for each additional CMG).
References:
Detailed steps on how to configure SCCM DMZ MP and DP:
https://www.systemcenterdudes.com/installing-sccm-dp-mp-sup-untrusted-domain/
https://configmgr.com/configmgr-cmg-and-the-dmz/
One way network connection from intranet to DMZ
https://archive.wmug.co.uk/wmug/b/r0b/posts/push-based-replica-management-point
Ports needed in SCCM DMZ
Complete list of ports needed in SCCM
Hi Rui,
Thanks for your contribution. That’s a brilliant post!
I am wondering if you allow any access from the DMZ SCCM back into a DC for authentications. I am assuming that the DMZ SCCM server is domain joined in this case.
I am actually in the process of implementing an SCCM DMZ IBCM in the same way as you did as secure as possible. There is actually 2 things I am really curious about from looking at your solution diagram:
1. How did you setup the SCCM SQL in order to get the reporting data synchronized between both without the need for the DMZ SCCM to talk to a DC in the Intranet for account authentication?
2. Is it possible to use the DMZ SCCM configured with a commercial SSL Certificate (e.g.: DigiCert, etc) instead of Domain SSL Certificate with only the Internet FQDN specified, and without adding hostname as a SAN?
For reference:
– Our DMZ SCCM has hostname like SCCM.localdomain.local and Internet FQDN like SCCM.internetdomain.com
Hi Bruno,
Our DMZ SCCM is in our DMZ domain, so it authenticates with the DMZ AD. It is still under the same forest, however, a child domain.
1. Two way communication for the port 1866 between the DMZ SCCM and the internal SQL is needed as one way SQL replication won’t work. It failed many times in my test. As for the authentication, I setup a local sql service account for authentication. Otherwise you have to enable the communication to the internal DC.
2. It is totally workable. You can have two certificates, on the IIS bindings, just bind the commercial SSL with hostname SCCM.internetdomain.com, and bind the internal certificate with host name SCCM.localdomain.local.
It is under “IIS Manager” – “Sites” – “Default Sites” – “Bindings”.
Hope that will fix your problems 🙂
Hi Rui,
Thanks! That definitely sheds some light on it.
We are trying to have it all done by having the DMZ Site System Server in the same AD Forest and Domain as the Intranet Primary Site server, but we only want to allow necessary ports. So, we’d be looking at not allowing DC access to intranet and we also have no plans to use RODC in DMZ either. Would you say that can be achieved? See questions below in case you are able to provide some advice here.
– About MP Replica – did you setup SQL replication in merge mode? Would replication be achievable with local service accounts instead of Domain User Accounts?
– What about CRL checks for DMZ Web Server or Internet Clients? Which route did you take for this? I know the clients would need to be able to access CRL in order to validate the DMZ Server Certificate and that the DMZ server itself would also need to check CRL to validate the clients certificate.
Any tips ? Your advice is highly appreciated!
Yes, it is achievable.
1. About MP Replica, it is achievable with local service accounts for sure, I have tested it working. I was using SQL replication pull mode(As our CIO wants the one way communication only for SQL and SCCM), which it failed and causes many times. I suggest you could another way to achieve this.
2. You can setup a OCSP for this. Build a web proxy in your DMZ, and allow the machines to check OCSP from the internet via your web proxy.
https://rui-qiu.com/active-directory/how-to-setup-ocsp-and-internet-access/