1. Cannot install SCCM agent via CMG MP
Recently I found out that I cannot install sccm agents on our DMZ zone, when I checked the ccmsetup.log, it showed that it is trying to grab the SCCM MP from AD instead of using our CMG address:
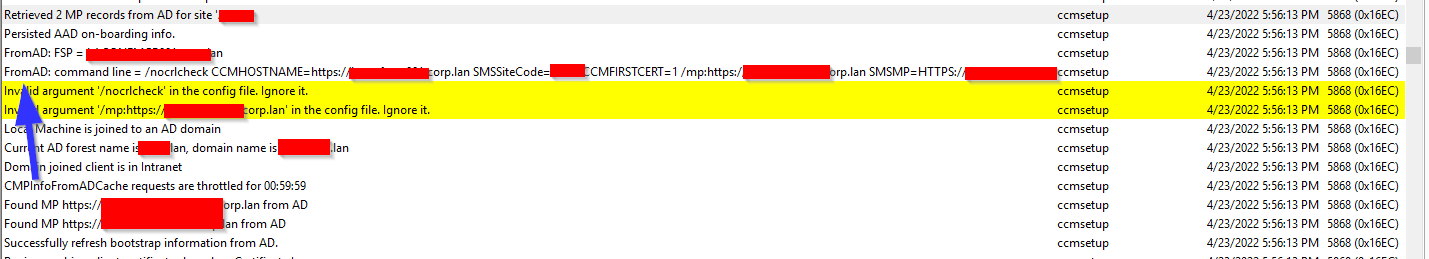
From my sccm install command line, it is
ccmsetup.exe /nocrlcheck /UsePkiCert CCMHOSTNAME=xxx.CLOUDAPP.NET/CCM_Proxy_MutualAuth/xxx SMSSiteCode=xxx CCMFIRSTCERT=1 /mp:HTTPS://xxx.CLOUDAPP.NET/CCM_Proxy_MutualAuth/xxx CCMALWAYSINF=1 SMSMP=https://xxx.CLOUDAPP.NET/CCM_Proxy_MutualAuth/xxxbut why the ccmsetup is taking the command line from the pic below, totally overwrote my SCCM installation parameters?
It turned out that the ccmsetup is taking the parameters from Client Installation Settings from our SCCM console here directly:
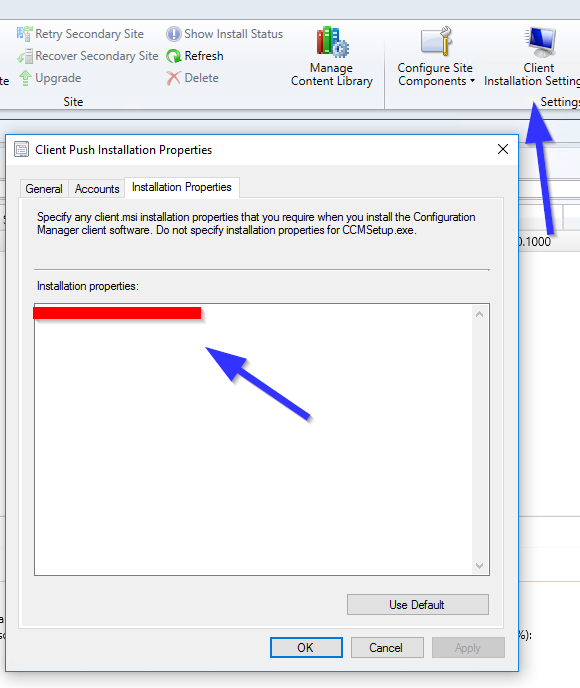
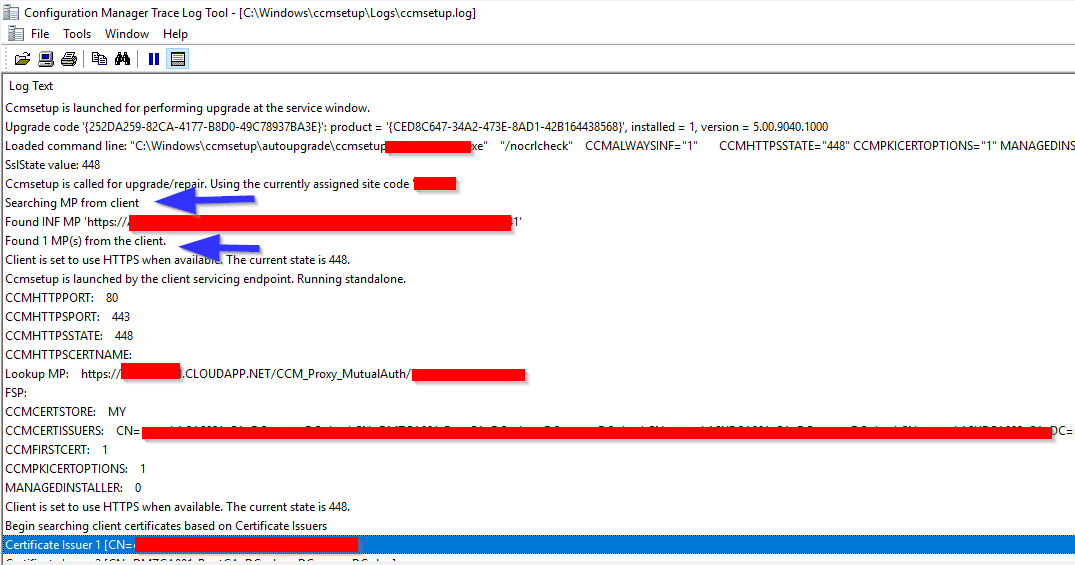
After I choose “Use Default”, the SCCM client can be installed correctly. You can see from this log that the MP is sourced from client directly instead of AD.
2.ADALOperationProvider.log Errors
If you see tons of red error messages from ADAL Operation Provider, and you are using PKI to authenticate on your internet mode only sccm clients, that’s normal. This log is trying to authenticate your machine with Azure AD credentials.
3.WINHTTP_CALLBACK_STATUS_FLAG_CERT_REV_FAILED is set
One day all of our internet only mode clients cannot reach to our CMG, and they are all offline from SCCM console. When I tried to manually re-install the agent, here is the errors I got from ccmsetup.log
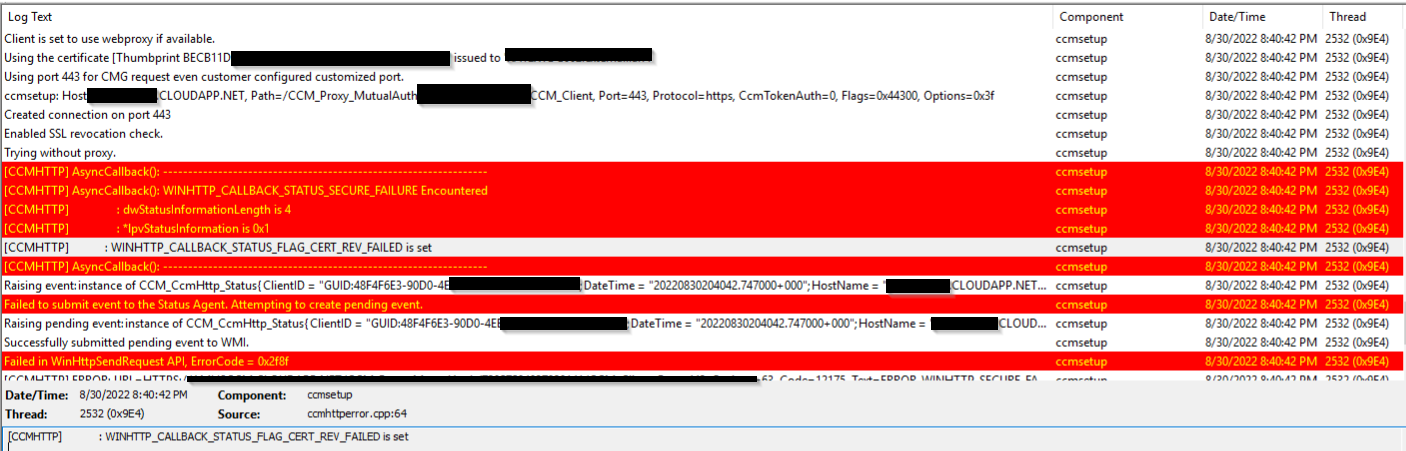
If you look at the log closely, the keyword is WINHTTP_CALLBACK_STATUS_FLAG_CERT_REV_FAILED is set. That means certificate revocation is failed.
We already disabled this in the CMG settings:
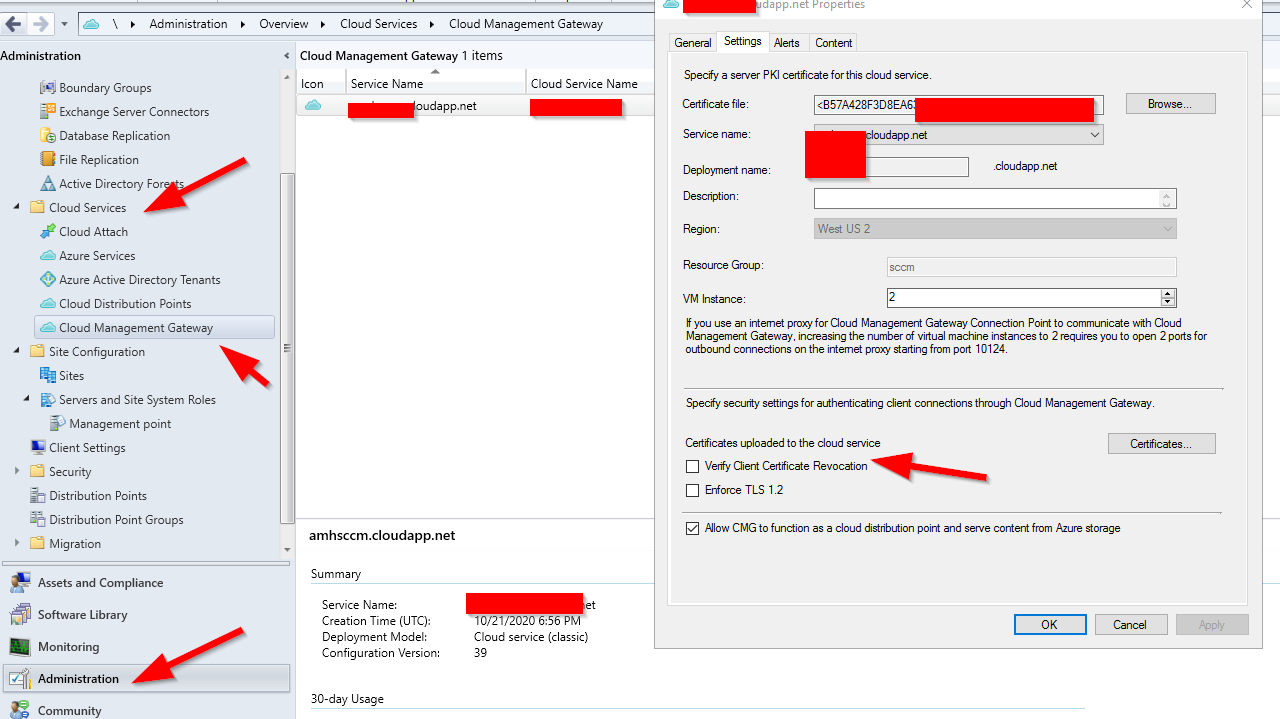
But just to make sure, I made these changes to the CMG( RDP into the CMG VM itself).
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL]
SendTrustedIssuerList 0
ClientAuthTrustMode 2
Also, these are the changes we need to disable certificate revocation check on the server connected to CMG:
netsh http show sslcert
If you see revolcation is enabled, you can use these commands to disable it:
netsh http delete sslcert ipport=0.0.0.0:443
netsh http add sslcert ipport=0.0.0.0:443 certhash=your_cert_thumbprint appid={your_app_id_no_need_to_change} certstorename=My verifyclientcertrevocation=disable
After that, reboot your server.