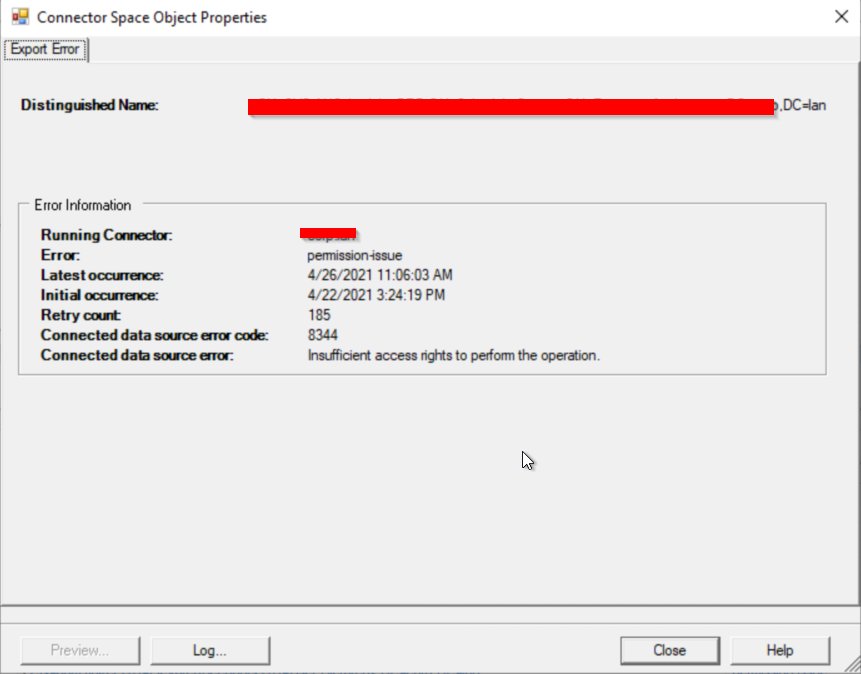
If you see some user has 8344 permission issues on your Azure AD Connector log, the fix is simple:
Enable AD Inheritance on all users in an OU and all sub OUs
<# Purpose: To enable inheritance for all AD users in the specified OU and all sub-OUs. Author: Michael Kenning ([email protected]) Version: 1.1 (release) Updated: 21 FEB 2015 Notes: Change variables as needed #>### VARIABLES ###$searchOU = "ou=OUNAME,dc=DOMAIN,dc=COM"### END VARIABLES ###$users = Get-ADUser -ldapfilter "(objectclass=user)" -searchbase $searchOU$changed = 0$same = 0ForEach($user in $users){ # -- Get the full path to the user object $ou = [ADSI]("LDAP://" + $user) # -- Get the security information for the user object $sec = $ou.psbase.objectSecurity # -- Change the security settings for the user if ($sec.get_AreAccessRulesProtected()) { $isProtected = $false ## allows inheritance $preserveInheritance = $true ## preserve inherited rules # -- Make the change! $sec.SetAccessRuleProtection($isProtected, $preserveInheritance) $ou.psbase.commitchanges() # -- Let the console know that the user was changed Write-Host "$user is now inheriting permissions"; # -- Increment the changed user count $changed += 1 } else { # -- Let the console know that the user didn't need to be changed Write-Host "$User Inheritable Permission already set" # -- Increment the unchanged user count $same += 1 }}# -- Give a summary of changesWrite-host "The number of changed users is $changed"Write-host "The number of unchanged users is $same"Additional Reference:
Azure AD Sync Connect issue with permission error 8344 – Microsoft Q&A